1. Use a ridiculously long password
There are two camps when it comes to password strength. One camp argues that password strength should be measured through complexity (at least 6 or 8 characters long and contain a mix of lower case/upper case letters, numbers, and special characters) while the other side insists that lengthier passwords are best. Personally, I’m siding on the latter. Even the FBI recommends using long passwords.
Instead of using a short, complex password that is hard to remember, consider a memorable passphrase like “GlobalWarmingIsRealLet’sPhaseOutCoalBaby”.
The longer the password, the greater the number of combinations. The greater the number of combinations, the lower the probability of guessing correctly your password. I hope you guys are convinced at this point because I’m not doing the math.
While we are already on the topic of passwords, did you know in March 2019 Microsoft dropped the password-expiration policies? This means that requiring people to periodically change their passwords is an ancient practice. When required to create a new password, people tend to write them down or just make slight predictable changes which defeats the purpose of making the changes to improve security. I'm just putting it out here in case you need this knowledge.
Using the same password for multiple websites though is still a big no-no.
So yeah, just use a ridiculously long but memorable password.
2. Stop trying to make money online
Before I get a lecture from my freelancer and legit online entrepreneur friends… I’m talking about the Nigerian prince promising to send you his inheritance, that FREE $1000 Amazon gift card that popped up while browsing your favorite kid-friendly website, or that time you won the US lottery jackpot without buying a ticket.
If it’s too good to be true, it must be a scam!
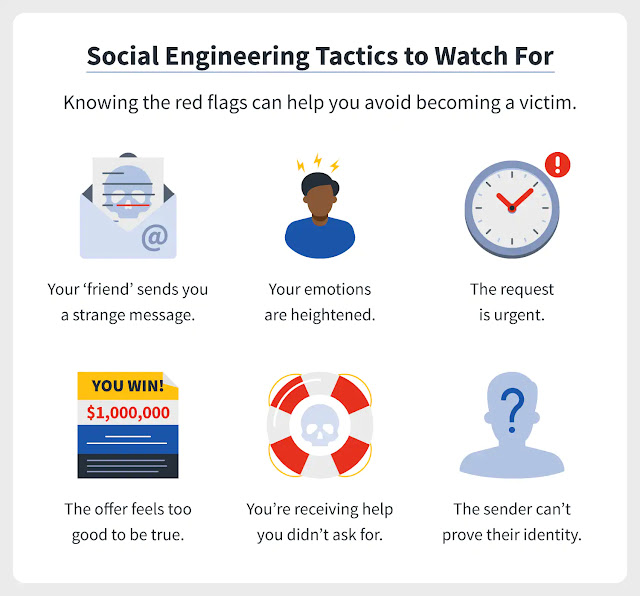
Most people’s mental image of a cyber security attack is that of someone typing lines of code on their laptop to take down a company but the number one cybersecurity threat when ranked is social engineering. That is, when people with malicious intent use psychology to manipulate other people into doing certain actions from a simple task of clicking a link to sending them money. They use our vulnerabilities like fear, desires, and even love to get what they want.
So the real number two tip is actually to always to be vigilant.
Be cautious online and offline. If you come across a suspicious email, chat, or text, have someone you trust to help you verify the authenticity of the message. You can also use Google search by simply copying and pasting the content of the message to the search. Observe the Scam Spotter 3 Golden Rules.
Again, if it’s too good to be true, it must be a fraud.
3. Don’t overshare on Facebook
...or on any other online platform.
We all have that one friend who made their social media accounts their diary. Not only can this be annoying but it can also put you at risk of cybercrime. Personally, I have friends who are victims of such shady schemes where a malicious person used their profile photos to extort money from others.
Protect your Personally Identifiable Information or PII. This includes your real name, address, birthday, email, ID numbers, medical records, bank account, and full-face photos. There is a huge list of dangers and consequences of oversharing on social media. Apart from potential identity theft, it's also an invitation for people to rob or stalk you IRL. Yikes.
I understand it feels good when people react or comment on our posts but those are just temporary bursts of dopamine. If you only use social media to connect with family and friends (not for business, school, or employment purposes), then there is no need for you to use your full name. Your loved ones truly care for you even if they can’t remember your birthday. We don’t need to see 12 copies of your selfie. Be more mysterious. Date in private. Change your privacy settings.
3. Don’t overshare on Facebook
...or on any other online platform.
We all have that one friend who made their social media accounts their diary. Not only can this be annoying but it can also put you at risk of cybercrime. Personally, I have friends who are victims of such shady schemes where a malicious person used their profile photos to extort money from others.
Protect your Personally Identifiable Information or PII. This includes your real name, address, birthday, email, ID numbers, medical records, bank account, and full-face photos. There is a huge list of dangers and consequences of oversharing on social media. Apart from potential identity theft, it's also an invitation for people to rob or stalk you IRL. Yikes.
I understand it feels good when people react or comment on our posts but those are just temporary bursts of dopamine. If you only use social media to connect with family and friends (not for business, school, or employment purposes), then there is no need for you to use your full name. Your loved ones truly care for you even if they can’t remember your birthday. We don’t need to see 12 copies of your selfie. Be more mysterious. Date in private. Change your privacy settings.
Okay rhetoric aside, here are some best practices to keep you and your love ones safe on social media without being a killjoy:
- Set your audience to friends only especially for posts where family photos and names are involved. Most banks use our mother's maiden name to verify our accounts. Attackers can easily stitch information together if you are a family of over sharers. Scammers can also make fake emergency reports to your family.
- Have some post delay especially when on a vacation. This can signal potential thefts that you are away.
- Don't post photos of documents or IDs such as passports, plane tickets, prescriptions, and vaccine cards. A teacher posted his PRC photo online once and someone used it to avail of an P800,000 loan without his consent.
There are a lot of use cases where PII is involved. If you have a best practice that everyone can benefit from, please drop them in the comments! We love to learn from our readers.
4. BONUS TIP: If you want to learn more about protecting yourself online, join the biggest cyber security conference in the Philippines.


Be equipped with cybersecurity know-how to rise above a crisis, make informed decisions, and win the war against cyber threats. DECODE 2021 will be on November 10-11.
DECODE is the premier cybersecurity conference in the Philippines hosted by Trend Micro, a global leader in cybersecurity. To know more about this event and to secure your slot for free, visit https://decodeph.com
#Decode2021 #DecodePH2021













Useful blog, it is very impressive.
ReplyDeleteChallenges of Cyber Security
Cyber Security Challenges
Cyber security can be described as the collective methods, technologies, and processes to help protect the confidentiality, integrity, and availability of computer systems, networks and data, against cyber-attacks or unauthorized access.MSPs or managed service providers can address vulnerabilities in your network before they are even exploited. By implementing these guidelines, MSPs can bolster their line of defense against people with bad intentions. Equilibrium Consulting provides best MSP Marketing Services in United States.
ReplyDelete